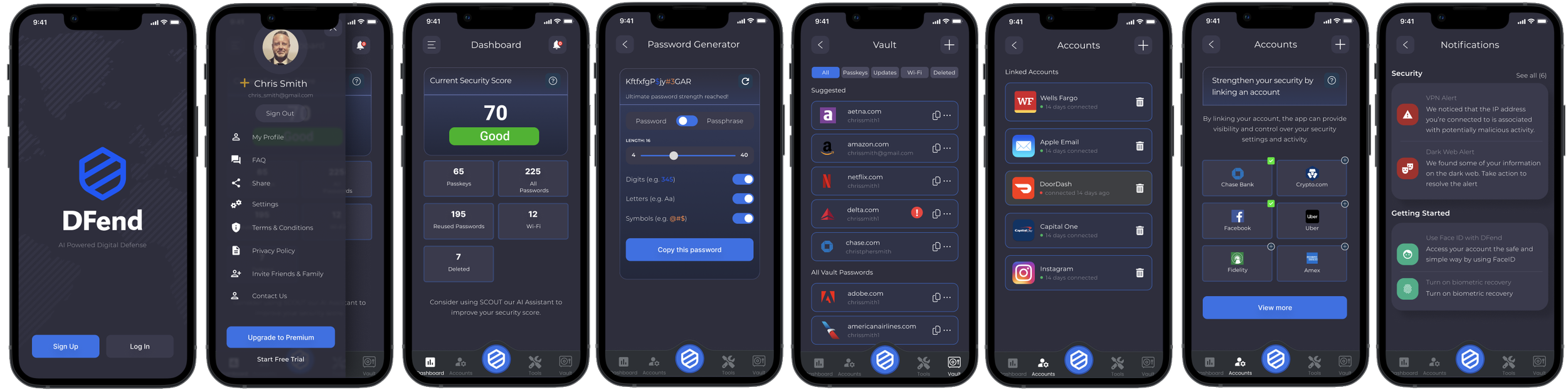
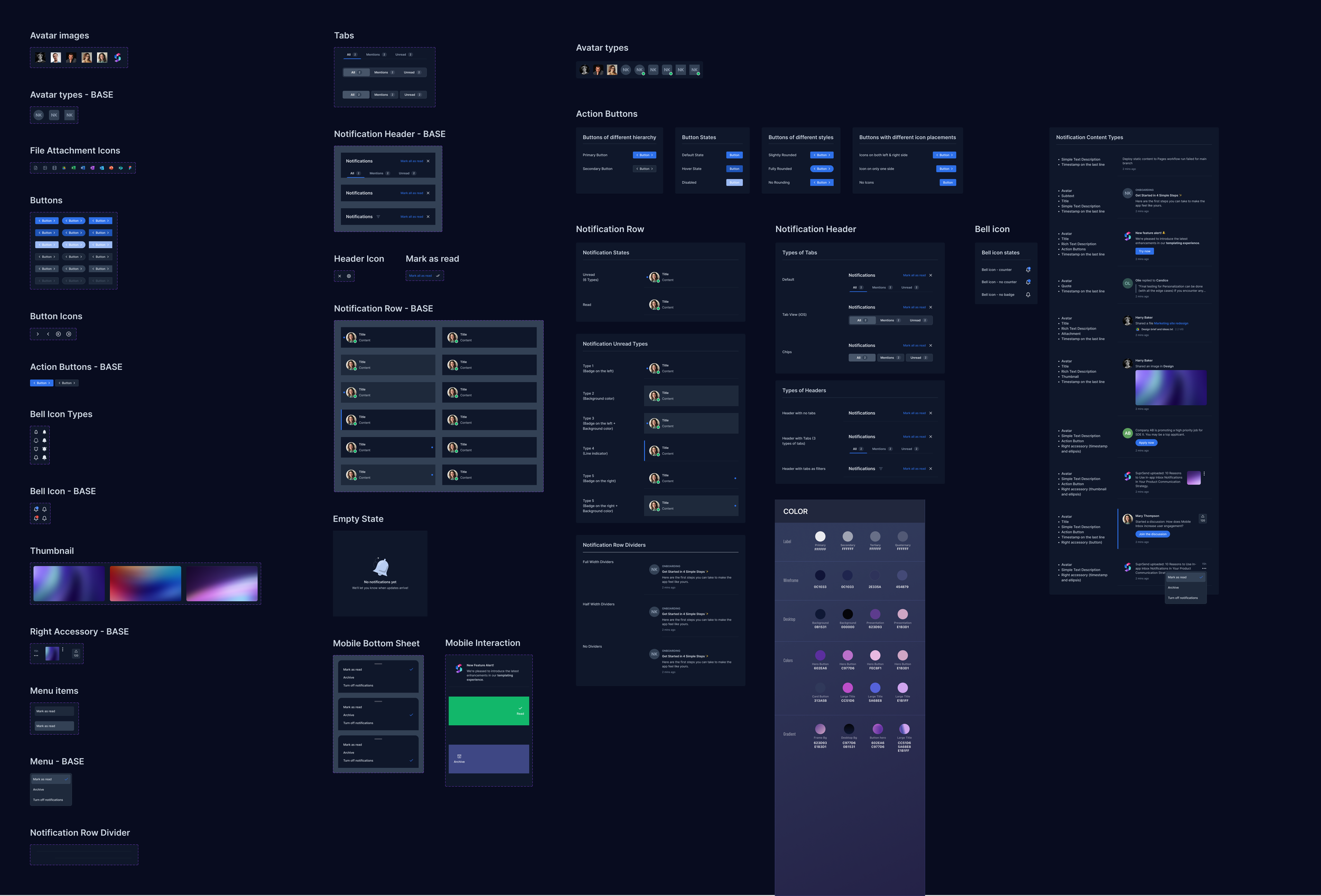
Context: AI-powered mobile cybersecurity assistant
Role: Principal Product Designer
Timeline: Nov 2024 – Jul 2025
DFend
Designing DFend: an AI-driven cybersecurity assistant that protects users proactively—before threats become problems.
DFend set out to rethink personal cybersecurity by shifting from reactive alerts to proactive protection. Rather than waiting for users to detect issues, DFend monitors patterns, identifies anomalies, and takes action autonomously—only surfacing notifications when needed.
The challenge: this was a net-new product with no existing blueprint, requiring a fresh UX foundation that established trust, balanced autonomy, and made advanced security feel simple for users of all technical backgrounds.
01
Understanding the Landscape
What Made DFend Different
DFend wasn’t another alert-heavy security app—it needed to operate quietly in the background while giving users confidence that the AI was making the right decisions.
Key themes from early exploration:
No Existing Baseline — A brand-new product meant designing an entire end-to-end flow from scratch.
AI Trust & Autonomy — Users needed clarity and comfort around letting AI take meaningful actions on their behalf.
Security-Critical Decisions — Account recovery, suspicious activity, and identity protections required zero ambiguity.
Conversational Interactions — A chatbot-like interface needed to handle complex logic while remaining approachable.
Wide User Spectrum — DFend had to support both highly technical users and those less familiar with cybersecurity.
02
Why Traditional Tools Weren’t Working
Defining the Core Problem
Users today are overwhelmed by security warnings, unclear terminology, and reactive tools that rely heavily on user action.
Patterns we identified:
Too Many Alerts — Traditional apps over-notify, leaving users unsure what’s actually important.
Unclear Risk Interpretation — People didn’t know how serious issues were—or what steps to take next.
Cognitive Overload — Security flows often require too much technical literacy.
Low Confidence in Automation — Users weren’t sure when to trust AI to “just handle it.”
These insights shaped the product’s defining feature:
a trust slider that lets users choose how much autonomy DFend should have—from “notify me first” to “handle it automatically.”
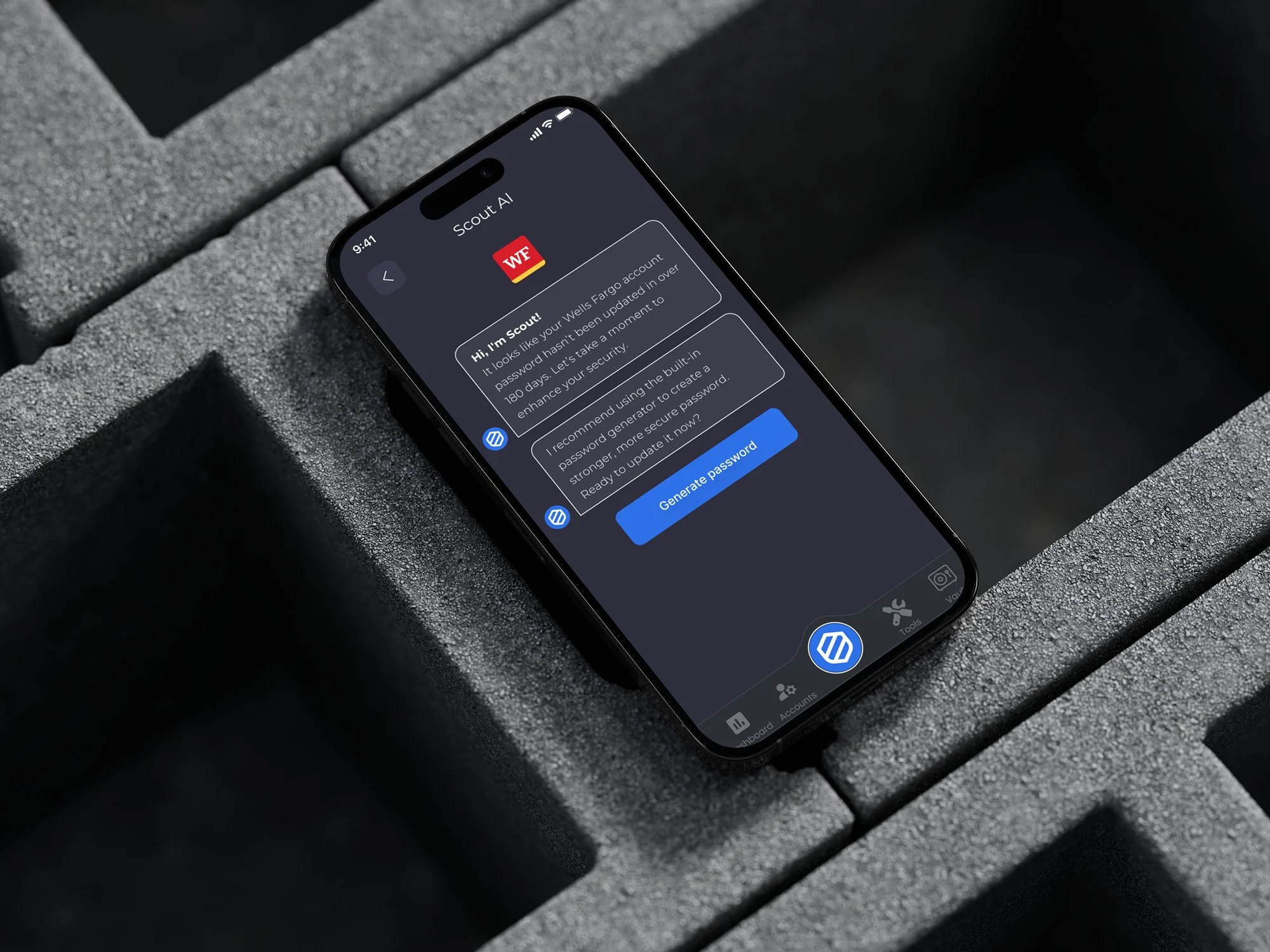
03
Designing a Clearer, Smarter Security Experience
What I Focused on
My goal was to make cybersecurity feel invisible, intelligent, and intuitive—powered by AI, grounded in user trust.
Reducing Complexity
Converted dense, security-heavy flows into clear conversational steps.
Designing for Autonomy
Built a threshold slider that lets users choose the level of AI control.Modernizing Visual Language
Created a mobile-first, security-forward UI that feels calm, confident, and familiar.Balancing Transparency & Silence
Notifications appear only when necessary; everything else happens in the background.Building Trust Through Patterns
Surface explanations, action previews, and clear opt-in moments when DFend acts autonomously.
The high-fidelity prototype on the left was used for user testing, flow validation, and production handoff. The DFend.app link provides a live redirect from the actual public domain, included here to demonstrate that the app was fully built and shipped.
04
Results & Impact
Creating a New Category of Proactive, AI-driven Personal Cybersecurity
The final experience reimagined digital safety as something users don’t have to manage manually.
Impact delivered:
Proactive Protection — DFend neutralizes threats before they disrupt users.
User-Controlled Autonomy — The slider empowered users to decide how much control to delegate.
Reduced Anxiety & Friction — Complex flows (password resets, suspicious logins, MFA) became clear, conversational actions.
Broader Adoption — Designed for all literacy levels, expanding accessibility of cybersecurity tools.
Future Scalability — Modular architecture supports subscription tiers, advanced monitoring, and premium add-ons.
Early prototypes showed users:
completed more tasks,
felt more secure,
and engaged more consistently than with traditional security tools.